RPKI Panel at M3AAWG
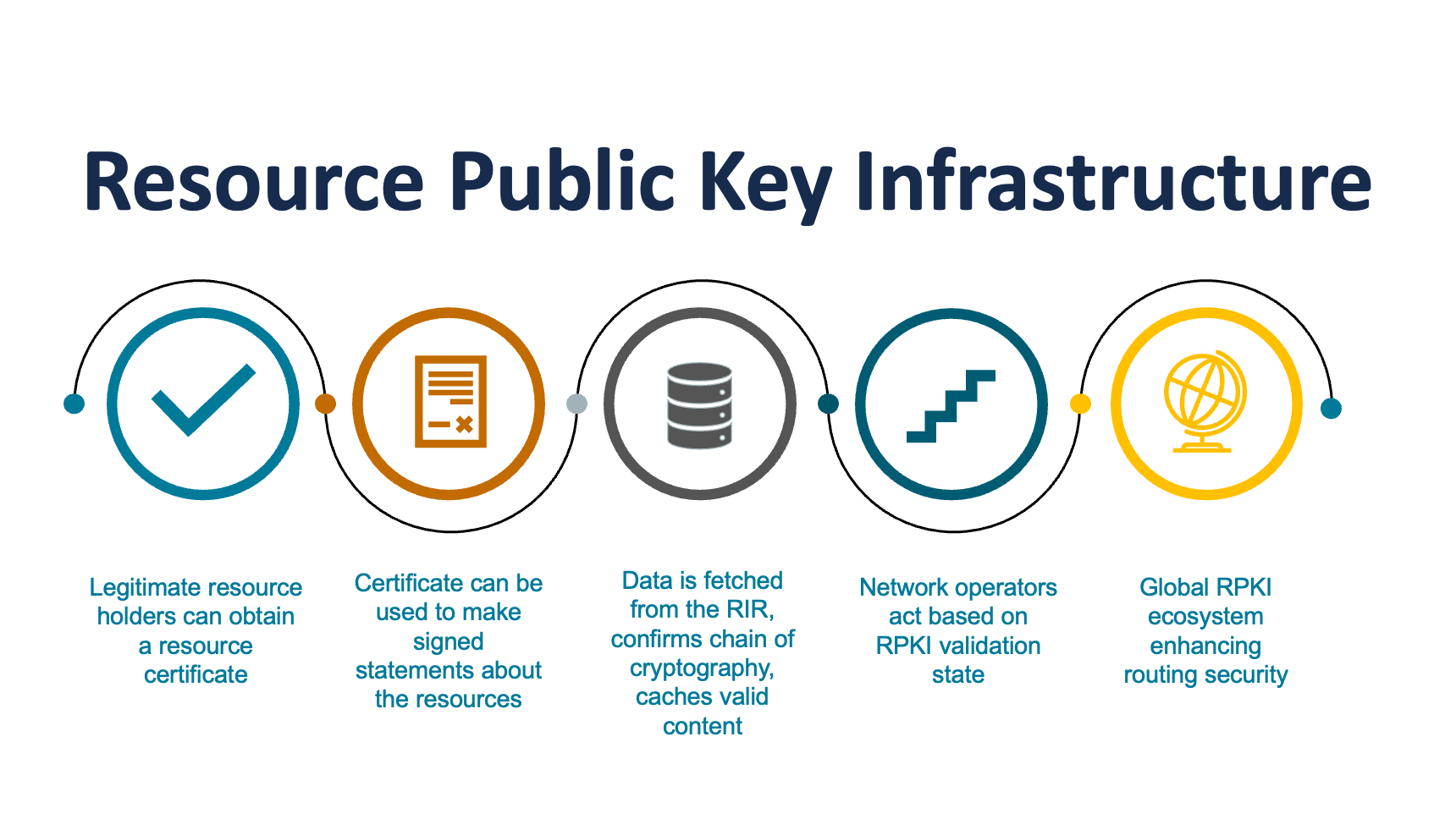
RPKI is an effective anti-abuse tool that helps to clean up Internet routing and make it more secure by working to prevent leaks and route hijacks for the Internet’s routing infrastructure. This was the key message of a panel presentation at the recent Messaging, Malware and Mobile Anti-Abuse Working Group 54 (M3AAWG) meeting in San Francisco.
About M3AAWG
M3AAWG is a global industry association whose members come together in a trusted open forum to collaborate on fighting botnets, malware, spam, viruses DoS attacks and other online exploitation. M3AAWG’s 200+ global membership includes ISPs, telecom companies, Email Service Providers, social networking companies, leading hardware and software vendors, security vendors and many others. Its work includes developing and publishing best practices, position statements, and training and education for the online community to help fight abuse as well as public policy advocacy for governments and Internet agencies. ARIN and the four other Regional Internet Registries (RIRs) recently became members of M3AAWG as part of our effort to further enhance our collaboration and engagement with industry partners.
Implementing RPKI Session at M3AAWG 54
As a co-Chair of M3AAWG’s Names and Numbers Committee, I organized and chaired a session at M3AAWG 54 titled “Implementing RPKI.” This topic stemmed from an open-round table session called “How to Encourage Adoption of RPKI to Help Stop Abuse of Internet Number Resources” that took place at a previous M3AAWG meeting.
Rich Compton, a Principal Engineer with Charter Communications and M3AAWG’s DDoS Sig Chairperson organized the round table, and both ARIN and LACNIC were active participants during the session. Follow-up discussions about the importance of RPKI as an anti-abuse tool prompted us to propose this as an agenda item for M3AAWG 54. This RPKI session featured Brad Gorman, ARIN’s Senior Product Owner, Routing Security, along with Rich Compton, each presenting rich and different perspectives on RPKI.
Making the Case for RPKI
Brad began with a high-level overview of routing security and then dove into the nitty-gritty of RPKI and how it can be an effective anti-abuse tool in helping to prevent route hijacks. Brad then went into the three current options for RPKI deployment — hosted, delegated, and hybrid — and walked through the components of each.
Brad also provided global statistics on RPKI deployment and ended with two real world examples of route hijacks (one malicious and one accidental) to demonstrate how RPKI could have helped to prevent them. However, he was careful to point out that RPKI is not infallible. Though it is based on best practices and best effort, he stressed that human error can sometimes still come into play.
How to Deploy RPKI
Rich began his presentation on RPKI from an implementer’s perspective, focusing on how and why Charter Communications deployed RPKI and some of the lessons they learned. He started with an example of an accidental route hijack that his company experienced and explained how RPKI could have helped to prevent the incident.
He then went over each of the steps Charter took to implement RPKI into its network which began with them creating test Route Origin Authorizations (ROAs) for lab prefixes, which they then tested in ARIN’s Operational Test and Evaluation Environment (OT&E). The steps they took to deploy their ROAs are:
- Identify the “source of truth”
- Determined what ROAs to generate
- Checked routers to see what they were advertising to peers
- Identify the deployment model
- Hosted – RIR handles everything
- Delegate – Org handles everything
- Hybrid – Org handles CA, RIR handles publication server/repository
- Set up the infrastructure
- Rich created a script to request, list and delete ROAs from ARIN’s API
- Created a script to monitor for INVALIDs and UNKNOWNs
- Compared ROAs to what they were routing
- Generate the ROAs
- Used the script to generate ROAs - started with a few, created them during a maintenance window
- Performed ping before/during/after ROA creation to IPs outside their network
- Operationalize management of the ROAs
- Looked for INVALIDS using a monitoring script
- As new prefixes provisioned, created new ROAs
- Must renew ROAs just like SSL certificates!
Rich also explained how Charter modified its peering agreements to require RPKI participation. Additionally, they are now requiring ROAs for the validation requirement for Bring Your Own IP (BYOIP) customers rather than the previously accepted Letter of Authorization (LOA). Rich concluded his presentation by discussing the lessons learned during deployment and Charter’s future plans for RPKI. One of their immediate goals is to migrate to ARIN’s new hybrid RPKI model rather than the hosted model they’re currently using.
We look forward to working with M3AAWG in the future and exploring how our organizations can continue to collaborate on ways to make the Internet safe and secure.
Recent blogs categorized under: RPKI
GET THE LATEST!
Sign up to receive the latest news about ARIN and the most pressing issues facing the Internet community.
SIGN ME UP →Blog Categories
Public Policy • IPv6 • IPv4 • Updates • Fellowship Program • Security • Grant Program • Caribbean • Outreach • ARIN Bits • RPKI • Internet Governance • Tips • IRR • Elections • Training • Guest Post • Data Accuracy • Business Case for IPv6 • Customer Feedback


